
The Aegis Approach
The Aegis-approach architecture leverages Type 1 Virtualization (SeL4) to split the mobile device functions into multiple virtual machines (VMs) to allow for greater operational integrity, more granular system control, and a reduced attack surface. Various rules of operation govern the interactions across functional areas and between virtual machines. These rules ensure that the system functions in very specific ways.
The HTC A9, Secured by D4, is the initial first-generation reference device for ultra-secure mobility and includes the following features:
- Boot integrity validation
- Isolated DIT (VPN)
- Isolated and controlled storage (eMMC)
- Isolated userland (Android OS)
- Isolated cryptographic functions (Entropy and Key Store)
This Aegis device is configured in such a way that communications to and from the device must traverse a VPN. This allows for sensitive areas like Entropy and Key Store to be protected from potentially high-risk areas such as the Android OS. The most current example is our second-generation solution leveraging the Aegis approach to designing secure and modular platforms that are now deployed on a mobile device is the Aegis Ultra-Secure Mobile Device.
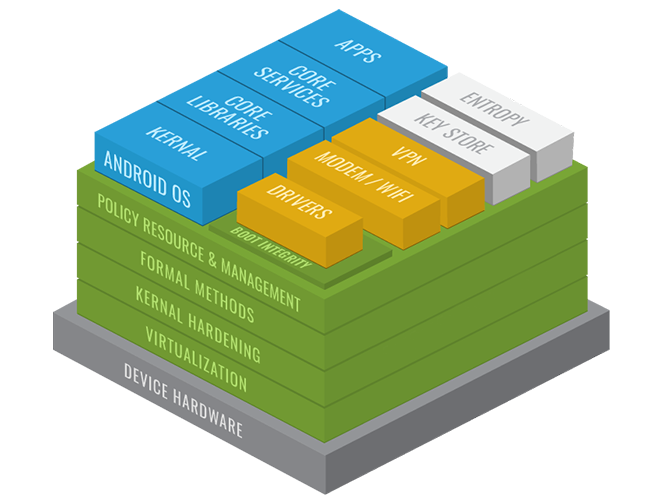
Components of Aegis Software and Aegis Hardware: Security Through Modularity
Aegis products focus on delivering towards ultra-secure mobility with SeL4 Virtualization, which is built on formal methods. These products help your organization conquer the challenge of security on untrusted networks. Primary components of Aegis hardware and software:
Aegis Secure Mobile SDK
The virtualization technology and framework that allows for the creation, configuration, and execution of the various function areas and virtual machines of a system.
Secure Boot
This feature validates and verifies which configurations and systems are to be booted and loaded onto a device.
Modular Hardware Platform
Device on which the Aegis Secure platform is installed. It consists of the CPU / SoC (central processing unit / system on a chip) and embedded components that make up a device.
SeL4 Virtualization: Functional Areas
- Android OS VM – This VM contains the Android OS including most of the general-purpose device drivers. It provides standard functions of the device from the end user’s perspective.
- Entropy VM – This VM is responsible for pseudo-random number generation for various cryptographic functions of the system. The reliable generation of cryptographically sound random numbers is vital to the system security and integrity.
- Key Store – Key Store is a VM containing cryptographic keys for encrypted areas of the system. Having these keys isolated from the rest of the system is critical for system-wide assurance.
- Secure DIT – The DIT (Data in Transit) VM processes all the data streams that traverse the modem and wi-fi areas. It encrypts this data and sends it across a VPN, protecting the data against eavesdropping and other attacks.
- Secure DAR – The DAR (Data at Rest) VM provides encrypted filesystem support for the various parts of the system. This ensures that data stored on the device is not accessible by unauthorized parties.
- Modem / Wi-Fi – This VM (within Android in the D4 Secure Base Reference Architecture) is where the data streams that flow across the device’s cellular modem or 802.11 wireless device are managed. By managing these flows of data, the device achieves more granular control over the data.
- Block VM – This VM controls the data streams that flow in or out of the device’s eMMC (physical storage). The isolation of storage functionality allows for highly managed control of data stored on the device.
The practical applications of the solution unlock the potential of your mobile device, while gaining defense-in-depth security. The device has the U.S. government NIAP Certification complete for CSfC compliance, including the MDF, VPN, and FDE Protection Profiles.
How Aegis Encrypting Retransmission Devices (ERDs) Level Up Your Ultra-Secure Mobility Solutions for Your End Users
The Aegis approach to developing a secure and modular platform is built in at the next generation of security for connected smart devices. By leveraging the Aegis approach to secure solution, platform security, device management, and other rich services are taken care of, so you do not have to – letting you build the next functional and innovative solution for your national security needs.
An Encrypting Retransmission Device (ERD) is a gateway in which you provide a distinct level of isolation for an end-user device from the ever present "dirty" networks that are constantly trying to attach to your end-user device. You could also leverage virtualization to create a Remote Personal Device that would also connect to your end-user device. This solution further isolates your end-user device from remote sessions or "dirty" networks and provides a mechanism to obfuscate certain functions one could leverage on an end-user device by using another form factor. Naturally, you could design your gateway to provide isolation to the myriad data access across your government (NIPR/SIPR), personal, public, or business networks.
The Aegis approach to creating secure hardware-based architectures leverages Type 1 Virtualization (SeL4) to split the gateway device functions into multiple virtual machines (VMs) to allow for greater operational integrity, more granular system control, and a reduced attack surface. Various rules of operation govern the interactions across functional areas and between virtual machines. These rules ensure that the system functions in very specific ways.
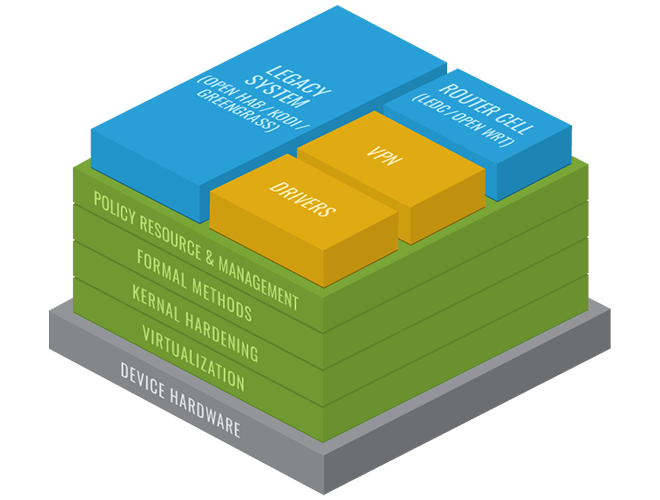
The Aegis software is built on an approach that leverages modular-based security systems that are much more effective at protecting networked devices from unwanted intrusion.
On top of the VPN, the ERD enables the local user to add the following to their end-user devices:
- A Protocol break that sanitizes the dataflow going in, reducing the threat from malicious attachments, and ensuring only clean data reaches your connected device
- A Firewall that can be tuned to only accept data from known IP addresses, and block data from any other addresses before it gets to your connected device.

Cloud Micro Services for Secure Internet of Things (IoT)
The Aegis Secure platform offers an optimal approach to the reliability, repair, and maintenance of IoT devices. Secure IoT examples include VPN, Firmware Over the Air Update (FOTA), Device Management, and more.

Integration Services for Aegis Secure Products
The Aegis Secure solution is designed to be easily integrated into your target device, however, you may require additional support. Riverside Research has experts fluent in embedded systems and embedded virtualization. These teams can help with integration support, driver writing and platform porting, and related contract software development, including low-level bootloader, standalone C applications, real-time OS, Linux or high-level software, such as Android. This support ranges across a full spectrum of requirements, including:
- Customization to meet the unique requirements of your device. This could include separation of drivers, adding unique security components, or creating unique configurations and user experiences as required by your use case.
- Staff augmentation to help deliver your project on time and under budget.
- Consulting design services for embedded systems product development for particular use cases specific to the NGO community, Department of Justice, or the Department of Defense.

Aegis Hardware and Software Support
Riverside Research provides dedicated software support for your Tier-3 support personnel via phone or email, enabling ultra-secure mobility for the next generation of devices.
Aegis Secure products meet CSfC compliance. The new industry standard is ultra-secure product solutions through modularity.
