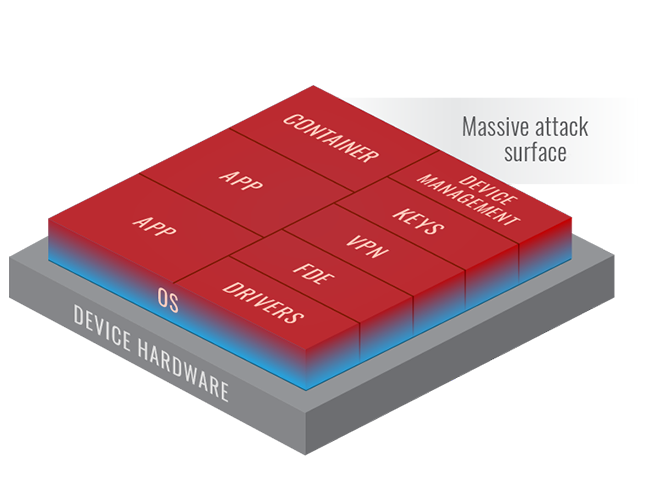
Aegis-branded Approach
An Aegis-branded approach to the development of secure products is the answer. The Aegis secure platform and solution use either or both Hardware Isolation or Type 1 Virtualization to design and assure a more secure and productive architecture.
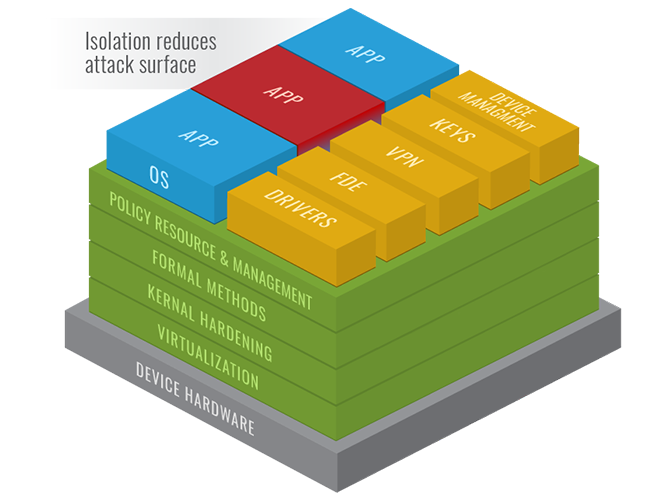
How the Aegis Approach to Designing Secure Software Works
The architecture isolates certain system processes and capabilities by leveraging Type 1 Virtualization to separate the functions into multiple Virtual Machines (VMs). It splits the system into multiple functional areas, allowing for greater operational integrity, more granular system control, and a reduced attack surface. Various rules of operation govern the interactions across functional areas and between virtual machines. These rules ensure that the system functions in very specific ways, as defined by the specific use case.
Key features of Aegis Secure Products:
Modularity
Multiple levels of containerization serve to isolate applications and components while enabling plug and play virtual machines and components, faster system development, and software reuse. This approach makes it possible to securely run legacy software together with updates and third-party software.
Formal Methods
Riverside Research only uses formal methods-proven virtualization tools. This is the only way to ensure that the virtualization tool is mathematically proven to perform as built. This is the newest standard for providing an "assured" level of security in the code that operates on the lowest level of your connected device.
Security
Aegis Secure Products are the industry’s most advanced Virtual Private Network (VPN), storage encryption technologies and device policies ensure defense-grade embedded security.
Value Added Modules – Additional layers of security can be added to D4 Secure to provide the highest degree of assurance that the device and data are protected, including:
- Full Disk Encryption (FDE) – A second layer of full disk encryption beyond the native encryption capability typically included in the operating system to provide double Data at Rest (DAR) protection.
- Dedicated Outer VPN – Using modularity to enable a non-bypassable outer VPN in support of end-user devices gives users the other half of the best-in-class inner/outer VPN tunnels.
- Nested VPN – A second VPN to the operating system, to run a truly nested VPN solution on the device, which provides double Data in Transit (DIT) protection.
Scalability
Aegis Secure Products provide the ability to concurrently run software with vastly different Operating Systems (OS) and platform requirements as well as a common set of software over a variety of different hardware devices. This speeds up development by eliminating the need to refactor or rewrite old code and easily supports new hardware.
Device Management
Aegis offers unrivaled capacity management and control facilitating Over the Air updates (OTA) at the platform level, supporting any OS, legacy, or third-party software.
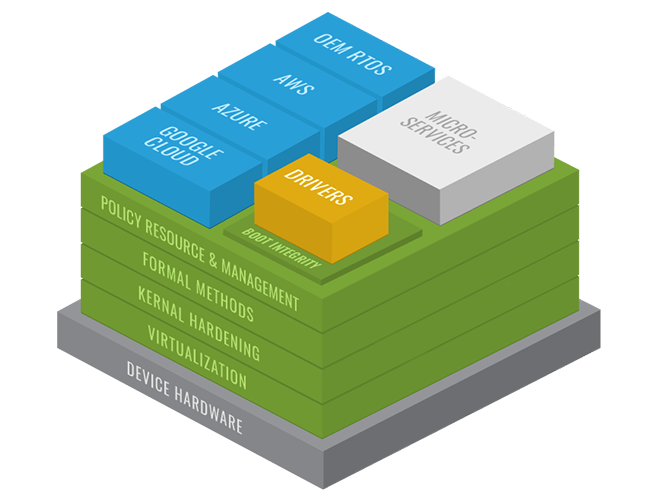
Modularity: A Foundation of the Aegis Approach to Secure Architecture
The Aegis approach to designing a secure solution provides the ability to compute anywhere, anytime while enabling faster response times and protecting the data collected and processed at the edge.
The approach in building Secure Products, our products leverage Type 1 Virtualization tools, such as SeL4, to modularize edge device functions into multiple Virtual Machines (VMs) to allow for greater operational integrity, more granular system control, and a reduced attack surface. Various rules of operation govern the interactions across functional areas and between VMs. These rules ensure that the system functions in very specific ways.
